- Mysql Sql Injection Cheat Sheet Github
- Union Sql Injection Cheat Sheet Github
- Sql Injection Cheat Sheet Github Example
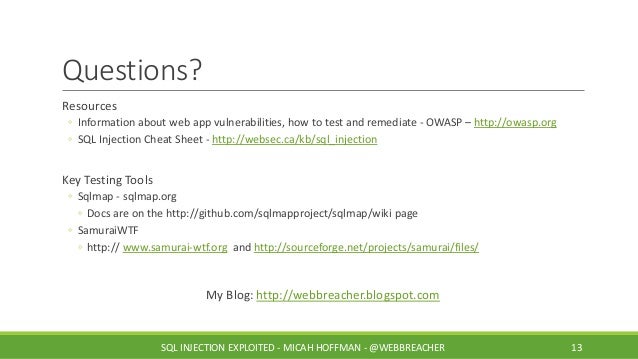
- Pentestmonkey Sql Injection Cheat Sheet
- Sql Injection Cheat Sheet Github Pdf
GitHub - kleiton0x00/Advanced-SQL-Injection-Cheatsheet: A cheat sheet that contains advanced queries for SQL Injection of all types. This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation 字符串连接. You can concatenate together multiple strings to make a single string.
This document has for objective to provide some tips to handle Injection into Java application code.
Sample codes used in tips are located here.
Injection in OWASP Top 10 is defined as following:
Consider anyone who can send untrusted data to the system, including external users, internal users, and administrators.
The following point can be applied, in a general way, to prevent Injection issue:
- Apply Input Validation (using whitelist approach) combined with Output Sanitizing+Escaping on user input/output.
- If you need to interact with system, try to use API features provided by your technology stack (Java / .Net / PHP..) instead of building command.
Additional advices are provided on this cheatsheet.
Examples in this section will be provided in Java technology (see Maven project associated) but advices are applicable to others technologies like .Net / PHP / Ruby / Python..
SQL
Symptom
Injection of this type occur when the application use untrusted user input to build a SQL query using a String and execute it.
How to prevent
Use Query Parameterization in order to prevent injection.
Example
References
JPA
Symptom
Injection of this type occur when the application use untrusted user input to build a JPA query using a String and execute it. It's quite similar to SQL injection but here the altered language is not SQL but JPA QL.
How to prevent
Use Java Persistence Query Language Query Parameterization in order to prevent injection.
Example
References
Operating System
Symptom
Injection of this type occur when the application use untrusted user input to build a Operating System command using a String and execute it.
How to prevent
Use technology stack API in order to prevent injection.
Example
References
XML: XPath Injection
Symptom
Injection of this type occur when the application use untrusted user input to build a XPath query using a String and execute it.
How to prevent
Use XPath Variable Resolver in order to prevent injection.
Example
Variable Resolver implementation.
Code using it to perform XPath query.
References
HTML/JavaScript/CSS
Symptom
Injection of this type occur when the application use untrusted user input to build a HTTP response and sent it to browser.
How to prevent
Either apply strict input validation (whitelist approach) or use output sanitizing+escaping if input validation is not possible (combine both every time is possible).
Example
References
- XSS)
LDAP
A dedicated cheatsheet has been created.
NoSQL
Symptom
Injection of this type occur when the application use untrusted user input to build a NoSQL API call expression.
How to prevent
As there many NoSQL database system and each one use a API for call, it's important to ensure that user input received and used to build the API call expression do not contains any character that have a special meaning in the target API syntax. This in order to avoid that it will be used to escape the initial call expression in order to create another one based on crafted user input. It's also important to not use string concatenation to build API call expression but use the API to create the expression.
Example - MongoDB
References
Log Injection
Symptom
Log Injection occurs when an application includes untrusted data in an application log message (e.g., an attacker can cause an additional log entry that looks like it came from a completely different user, if they can inject CRLF characters in the untrusted data). More information about this attack is available on the OWASP Log Injection page.
How to prevent
To prevent an attacker from writing malicious content into the application log, apply defenses such as:
- Filter the user input used to prevent injection of Carriage Return (CR) or Line Feed (LF) characters.
- Limit the size of the user input value used to create the log message.
- Make sure all XSS defenses are applied when viewing log files in a web browser.
Example using Log4j2
Configuration of a logging policy to roll on 10 files of 5MB each, and encode/limit the log message using the Pattern encode{}{CRLF}, introduced in Log4j2 v2.10.0, and the -500m message size limit.:
Usage of the logger at code level:
Example using Logback with the OWASP Security Logging library
Configuration of a logging policy to roll on 10 files of 5MB each, and encode/limit the log message using the CRLFConverter, provided by the OWASP Security Logging Project, and the -500msg message size limit:
You also have to add the OWASP Security Logging dependency to your project.
Usage of the logger at code level:
References
- PatternLayout (See the
encode{}{CRLF}function)
- Log Forging - See the Logback section about the
CRLFConverterthis library provides.
Dominique Righetto - dominique.righetto@owasp.org
Dave Wichers - dave.wichers@owasp.org
Studying from various sources for Offensive-Security OSCP. I would like to make my own cheatsheet for the exam.
Enumeration
Enumeration is most important part. All finding should be noted for future reference. Without enumeration, we will have hard time to exploit the target.
DNS Enumeration
Forward Lookup brute force to find ip addres of host:
Reverse Lookup to find hostname:
Zone transfer and enumeration using Kali tools
Enumerate using Nmap
Port Scanning and Service Enumeration
Filter all open ports for nmap script scanning:
Automated Enumeration Script
Download: https://github.com/21y4d/nmapAutomator
Other Enumeration Command
Pentesting Specific Service
Port 21(FTP) Open
Scan FTP with Nmap
Login and Upload backdoor
Port 22(SSH) Open
Banner Grab
Quick Brute Forces
Port 25(SMTP) Open
Enumerate Using netcat. Used for username Enumeration. Useful for brute forcing
Port 53(DNS) Open
Enumerating with nslookup,dig and gobuster:
Other tools to try:
Port 79(Finger) Open
If finger service is running, it is possible to enumerate username, and useful for brute force purpose.
Port 80/443(HTTP/HTTPS) Open
What to check?
- Manually Browse Common Files.
- Identify Technology. Search Vulnerability with identified info.
- Gather information from SSL.
- Check if it has any proxy related vulnerability.
- Directory, Sensitive files brute force and spider any discovered directory.
- May need to find out the hidden parameters.
- Find all inputs point.
- Find subdomains using dnsrecon or dnsenum.
View sources, and also Browse Manually
Identify Technology with whatWeb
Scan with Nikto
If any CMS identified
Brute Force Directory and Files
- First use small common wordlist
- Then Big Word list
- Try with CMS related wordlist
Word list File to brute forces:
Brute force with Gobuster
Password brute Forcing(wordpress example)
LFI and RFI
If the URL parameter has file name, we can try to vulnerability for LFI/RFI. We should request invalid file and see if any error is displayed!
LFI Can execute code!
Send our malicious code using CURL or Burpsuite or even netcat:
Now execute command:
Command Execution
If found any parameters or input fields, we can try for command execution. Test Every parameters and input fields with these payload(Better to use burp suite intruder):
Reference and more payload: https://github.com/payloadbox/command-injection-payload-list
SQLi for Login Bypass
If any login page found, should be tried to bypass password check. These payload copied from: https://github.com/payloadbox/sql-injection-payload-list
CheatSheet:
MSSQL INJECTION: https://perspectiverisk.com/mssql-practical-injection-cheat-sheet/
MYSQL INJECTION: https://perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/
Exploit WebDav
If one method fail, another should be tested. If nothing work, Find different exploit!
Method 1:
Method 2:
Method 3:
Reference
File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion
SQL Injection: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/SQL%20Injection
Command Injection: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection
Port 110(POP3) Open
Found an user login information?
Port 111 (RPCINFO) Open
Connect with Null session.
Port 137,138,139 Open
Port 445(SMB) Open
Vmware workstation free download mac. There is a big chance getting sensitive information with SMB. Need to check everything carefully!
Enumerating SMB
Connecting to share without password(Anonymous login)
Login with Password
Port 389(LDAP) Open
Port 1433(MSSQL) Open
Reference: https://book.hacktricks.xyz/pentesting/pentesting-mssql-microsoft-sql-server
Quick brute for pass “SA” password
Connect to MSSQL Server:
Enable xp_cmdshell:
Execute System Command:

Port 2049(NFS) Open
Enumerate shares
Mount shares in Local Machine
Mysql Sql Injection Cheat Sheet Github
After mounting the filesystem if don’t have read/write permission, we need to edit /etc/passwd and change UUID:
Now we can write files to the target fold of the network filesystem. For example:
Port 3306(MYSQL) Open
Port 3389(RDP) Open
Connect to RDP
Brute force if a valid username found:
Add user to RDP Group
Port 5900/5800(VNC) Open
Scan with nmap
Connect from Kali
Password Attack
Sometime we need to do password guessing(We should!). For better success rate we need a good password dictionary. Also we should search for default credential online!
I have collected some Username and password for quick brute force, usually used for CTF. These list could be used to exploit weak password. Uploaded in GitHub:
Default Username: https://raw.githubusercontent.com/bytefellow/pentest/master/common-username
Default Password: https://raw.githubusercontent.com/bytefellow/pentest/master/common-password
Common password
Generate Password with cewl

Brute Forcing with Burp
If it is an web form we can brute force in intruder and match grep. Some screenshot from burp suit:
To brute force web form with the hydra, we need to grab the post data from the burp suite carefully. Otherwise, we will get false positive and waste lots of time! I tried to brute force otrs and it worked.
Brute Force With Hydra
Vulnerability and Exploitation
I believe finding vulnerability for the OSCP exam machine would be simple and easy. All enumeration previously should be noted! Version detection using and Web CMS version is most important to find exploit.
Find Vulnerability with Nmap

Using Searchsploit
Find Exploits using Google
Three kind of search should be enough to find an working exploit Free cac reader software for mac.
Working with Public Exploits
A public exploit might be coded in python, ruby, c/c++ or any other language. Before executing the exploit:
- Read the instruction Carefully.
- Edit Target address, Reverse connection ip and Ports.
Working with Shell
We may get shell, after exploiting some vulnerability. Now what?
Backdoor Files in Kali
Kali already has some web shell.
Quick Shell in Different language
Here it is: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Generate with metasploit
Upgrading Shell
Listening for Connection
Upgrading Shell when received connection!
Running Python http Server
Uploading Shell/File
After getting shell, we may need to upload additional files or stable backdoor.
Transfering file in Linux
Transfering file in Windows
Transfer file with impacket samba script
Piviot/Tunnel/Port Forwarding
- -L = Kali’s Port
- -R = Kali Port
- $ip:3306 is the port from target
Local Port Forwarding
Have SSH access with low privileges? and There are some ports open internally? Try Local Port Forwarding:
Remote Port Forwarding
No SSH Access but limited shell? Also some weird port is open? Upload plink and Try Remote port forward with plink
Connect to the the tunneled port:
Union Sql Injection Cheat Sheet Github
Dynamic Port Forwarding(Socks4)
Dynamic Port Forwarding from victim machine(Socks Proxy):
With Dynamic Port Forwarding We can access/browse any ip range of the victim machine. We just need to configure proxychains.conf as follows:
Now we can use any application through proxychains… such as:
Port Forwarding with Plink.exe
Remote Port Forwarding using Plink. Needed When we don’t have access to specific port on on target box!
Common Issue
Correct permission for SSH Key?
Load key “id_rsa”: invalid format ?
Try Removing additional space. Also keep the public key in the same directory of private key. We may get the warning, but it should work!
Sql Injection Cheat Sheet Github Example
Unable to negotiate with x.x.x.x … no matching key exchange method found
SSH Error:
Solutions:
Practical Exploitation
Exploiting NFS and FTP
I have done enumeration with nmapautomator. Found NFS and ProFtpd 1.3.5 is running. Can i download excel on my mac. But no HTTP. The exploitation step was:
The network File system mounted but does not have any contents. FTP version is vulnerable. So i had to exploit it manually(https://www.exploit-db.com/exploits/36803):
Pentestmonkey Sql Injection Cheat Sheet
This way, I was able to successfully exploit the system without directly using any tools!
Exploiting Jenkins Server
Was able to login as user admin and password admin. Then I have navigated to Manage Jenkins>>Script Console and pasted this code for reverse connection:
Clicked run and got shell!
Sql Injection Cheat Sheet Github Pdf
More Example: https://www.bytefellow.com/quick-initial-foothold-in-10-htb-machine/
